When we deploy virtual machines in Azure, one of the most important aspects to consider is the security of these machines.
If we have to access them to manage them, we have several options:
- Assign them a public IP: In this way we can access them via SSH (Linux machines) or RDP (Windows machines). To minimize the attack surface, it is recommended to configure the NSG (Network Security Group) to allow this access only from our public IP. If we do not do so, shortly after being active, this machine will receive attacks from multiple bots that will try to compromise our virtual machines. If we constantly change the public IP, because we access through a data line, or because we have to travel a lot, it’s not a very efficient solution because we will have to change the NSG every time we connect to the machine.
- Using a load balancer with NAT rules or other intermediate device, even from third parties such as a proxy, an application gateway, etc. The main drawback of this solution is the cost of this intermediate device. It would be necessary to analyse each situation to know if it is profitable.
- Using JIT (Just In Time) Access: It is another way to reduce the attack surface by automatically creating rules in the NSG when a user with the necessary privileges wants to access the machine. Again, the downside is cost, since JIT is part of the Azure Security Centre but is only available at the Standard level and not at the basic level.
- Jump machine: We can create a virtual machine in the same network where the rest of the machines are and that is the only one with a public IP. From this machine we access the others that will not have a public IP. The disadvantage is again the cost of having another machine and that will have a public IP, so it is exposed to outside attacks.
A solution similar to the jump machine, but without having to create a virtual machine, is Azure Bastion Host. This service allows us to access - via SSH or RDP - the machines of our virtual network from the Azure portal itself. It is a service managed by Azure, so we do not have to take care of maintaining a virtual machine (NSG, updates, user authentication, etc.) It also has a cost, which we can see in:
https://azure.microsoft.com/es-es/pricing/details/azure-bastion/
So, it would be necessary to analyse if this option is profitable.
Let's see how we can configure Azure Bastion Host to access two machines that we already have created. These machines are on the same virtual network, but on different subnets, and do not have a public IP:
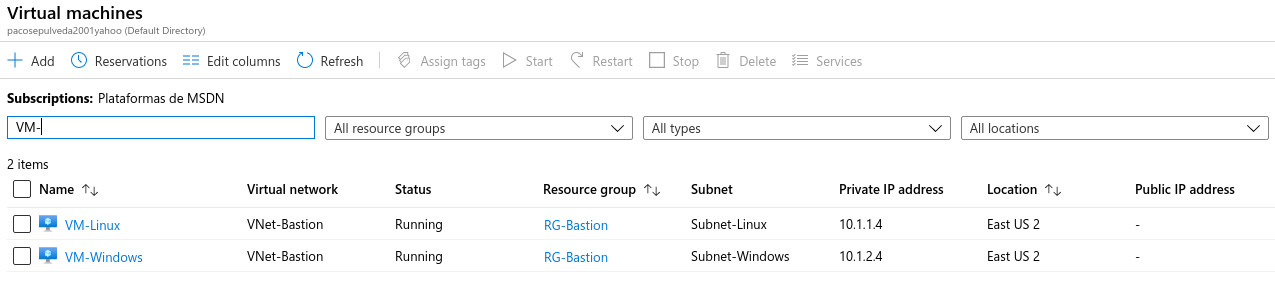
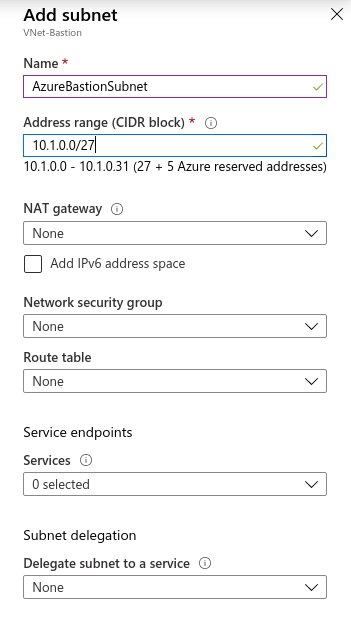
The first step in configuring Azure Bastion Host is to have a subnet within the same network as the machines we want to access. This subnet must meet the following requirements:
• Its name must be "AzureBastionSubnet".
• Must not be in use.
• Must have a 27-bit or less mask.
We create a subnet with the following characteristics:
And now we can start the creation of the Bastion Host:
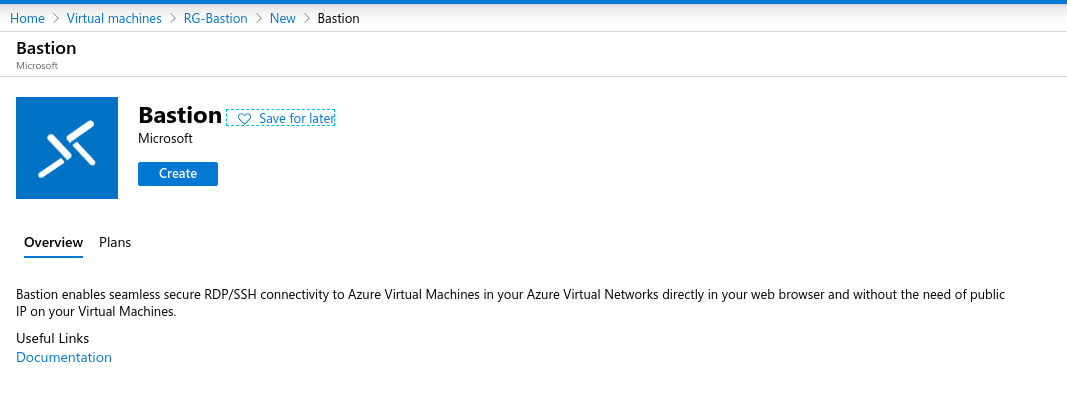
As we can see, it is very easy to create the Bastion:
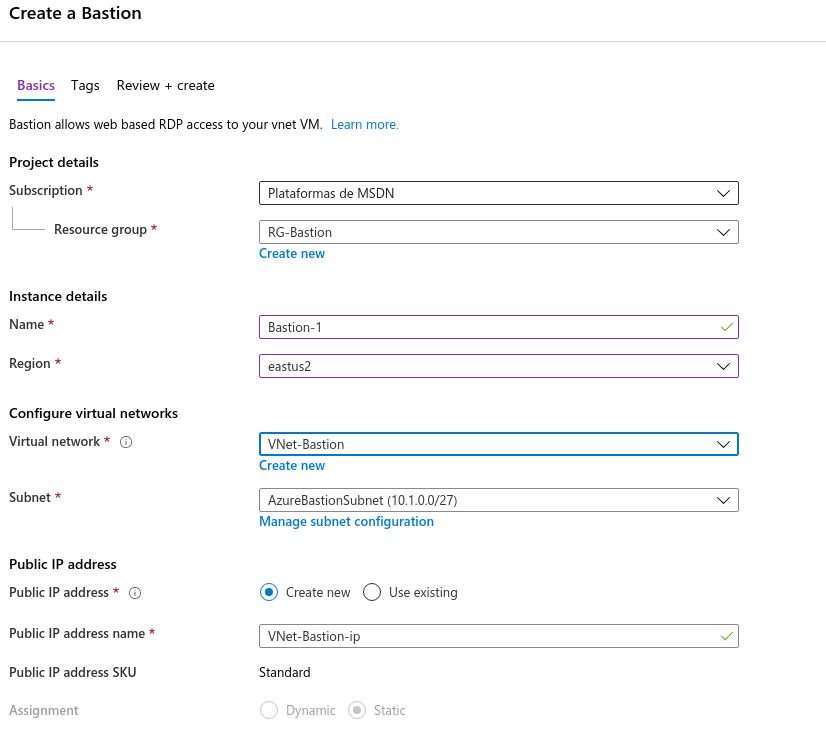
Once the Bastion is created, it is very easy to use it to access the machines:
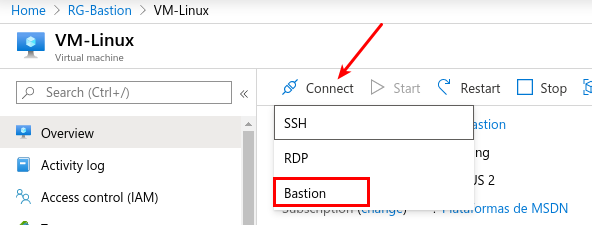
Just go to the machine we want to access and click Connect and select Bastion:
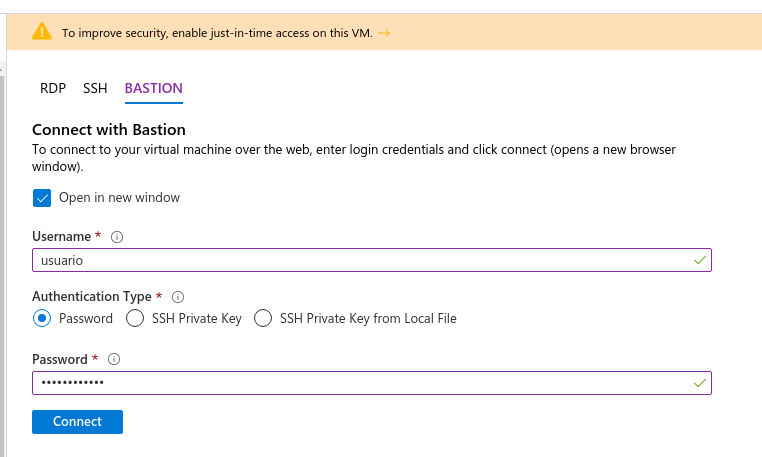
We should then input the credentials and click on Connect. We must take into account that, if we have a pop-up blocker in the browser, it might block the window that will open:
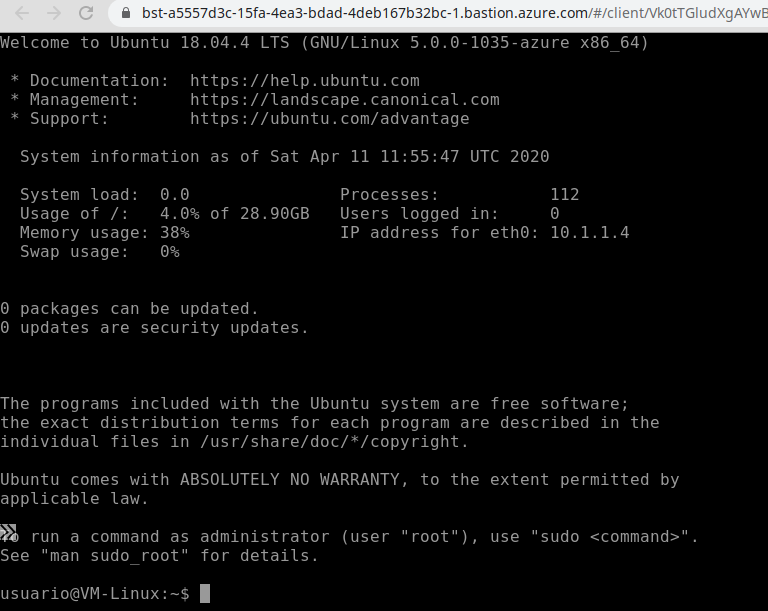
And now we have SSH access to the Linux machine from the Azure portal:
In the same way, we can have RDP access to the windows machine:
And in this way we can access virtual machines without them having to have a public IP, which increases their security.





